“There’s no real separation between the real world and the Internet. What we’ve begun to see now is a militarization of that space.” —Jacob Appelbaum, interview with VICE, 6 October 20131
I’ve been thinking a lot about this quote from Jacob Appelbaum for a few reasons. One is that it succinctly acknowledges that the Internet is a spatial construct as much as it is a social one. For the past year, I’ve been trying to see the Internet—by which I mean I’ve been trying to find, map, and understand its infrastructure and, through that infrastructure, understand the institutions and power systems that govern the network.
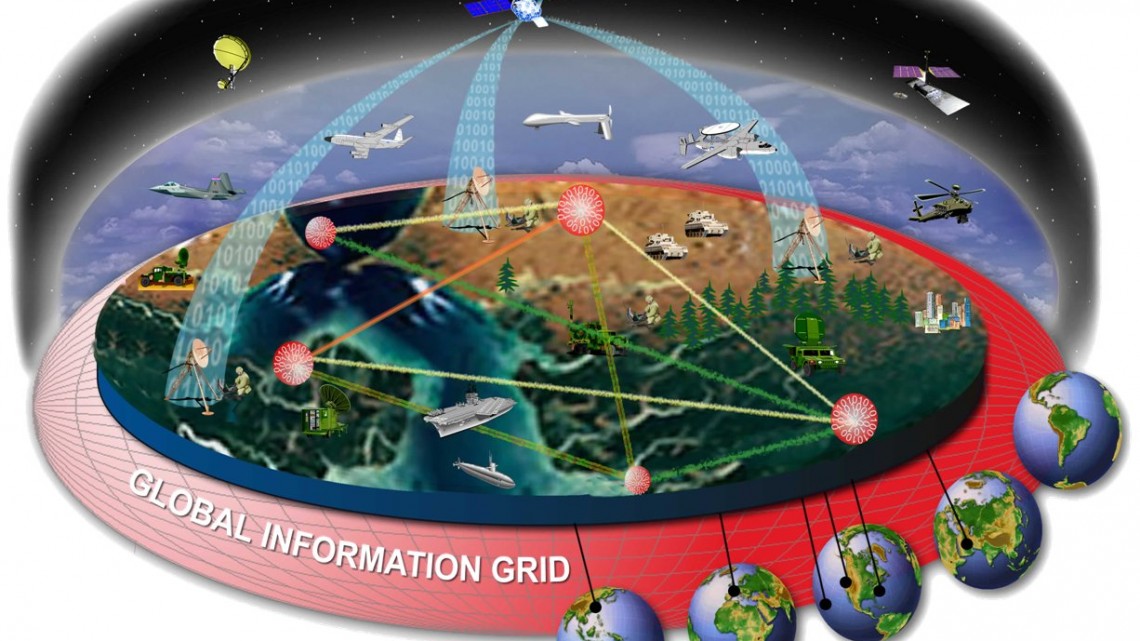
Another reason I’ve been thinking about this quote is that I’ve been trying to imagine what a fully militarized network space actually looks like. If an Internet of Things is the series of protocols through which networked objects talk to each other, what is the equivalent for networked defense systems? What defines an Internet of Wars? While trying to envision this network space, I realized that it technically already exists. The U.S. Department of Defense has its own networks, and its own network of networks. In trying to understand what an Internet of Wars actually looks like and how it shapes the Internet, you can’t do much better than the history and constituent parts of the Global Information Grid (GIG), the Department of Defense’s system that connects all of the military’s networked systems to each other.
The GIG’s networks span a wide spectrum of DoD agencies. Many of these networks are under the jurisdiction of the Defense Information Systems Agency (DISA), a division of the DoD that began in 1960 as the Defense Communications Agency and created the original (and still in use) hotline system that directly connected the Oval Office to the Kremlin in 1963. Two of the networks maintained by DISA are NIPRNet (Non-secure Internet Protocol Router Network) and SIPRNet (Secure Internet Protocol Router Network), networks briefly in the news following Chelsea Manning’s release of thousands of secret documents (downloaded from secure government networks, via SIPRNet) to Wikileaks. SIPRNet, NIPRNet, the Joint Worldwide Intelligence Communications System (JWICS), and several other secure, acronym-heavy networks make up the DISA’s Defense Information Systems Network (DISN). The GIG connects DISN to all the other networked systems that the military operates—satellites, radios, drones. The GIG is network-centric warfare made manifest: a protocol that allows for each constituent dataset, weapon, or communications tool to be used as building blocks in defense systems greater than the sum of their parts.
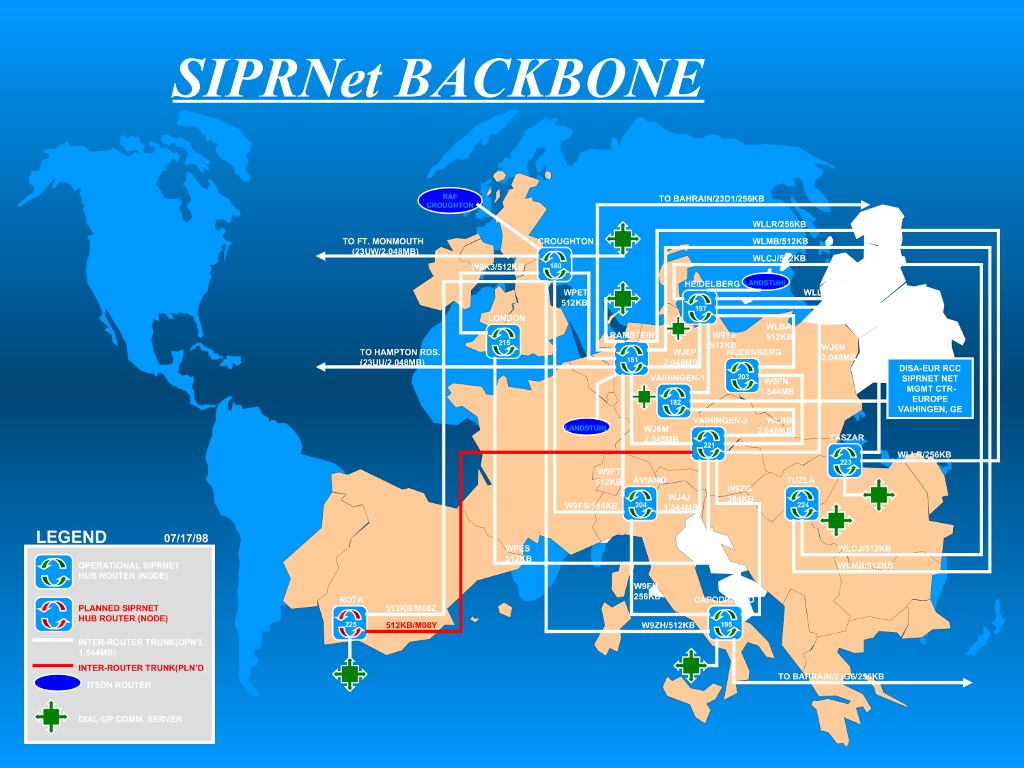
Computer Weekly, Drone Kill Communications Net Illustrated, http://www.computerweekly.com/blogs/public-sector/2014/06/-siprnet-backbone—europe.html. Courtesy of the Internet.
The idea of a government maintaining a parallel network for internal communications and documents doesn’t sound that staggering (banks do this for high-frequency trading, universities do it for research, cities do it at a much smaller scale) until you realize the scale at which a superpower sovereign military operates, the kind of infrastructure such a scale entails, and how rapidly that infrastructure has grown in the past fifteen years. One way to get a grasp of the scale and scope of the DoD’s network infrastructure is to search through federal DISA contracts—in addition to cloud infrastructure support and operations services, one finds RFPs for pulling fiber and building submarine cables between military bases.
One of those cable contracts was used by human rights organization Reprieve to argue that the company British Telecom (BT) essentially facilitated an extrajudicial murder program. The contract, issued in 2012, is for a cable network connecting RAF Croughton in the U.K. to Camp Lemonnier in Djibouti—a military base where the U.S. launched a number of its drone strikes in Yemen. The contract specifies use of KG-340 devices, which use NSA-specified encryption algorithms. The GIG is the means by which drones can talk to base stations, satellites, and the men in distant military bases deciding whether or not to fire on civilians. While a lot of networked objects make up the GIG, cables in the ground are the backbone of this entire system. Essentially, Reprieve made the argument that by providing that backbone, BT was a participant in the maintenance of an illegal, extrajudicial killing program.
The British government rejected Reprieve’s official legal complaint, arguing the contract alone could not “show a specific link between the communications service provided and the impacts of drone operations.” BT argued that it merely builds the cables;
that they are not responsible for the use of communications secured to NSA standards. This attitude is alternatively a show of bad faith or displays a horrifying lack of self-awareness on BT’s part. It also poses the question of how far the line of complicity extends. How much responsibility does any company or individual bear for merely laying the cable, merely writing the protocol, merely making the trains run on time?
And how exactly can any infrastructure provider not be complicit when the networks it is building have been so explicitly weaponized? In a slide deck from a defense contractor about securing fiber infrastructure, I came across the following quote from a DISA strategic plan written in 2006 (emphasis mine): “Our Command & Control Networks are truly being transformed into a weapon system as they get leveraged more and more by our soldiers—and as such, need to be protected from the increasing focus and efforts of our enemies to attack them using any & all means . . .” This is to say that cyber war’s doctrine isn’t merely that the network is a means to a weaponized end, but that the DoD apparently views its own networks as a weapons system. In this context, the hyperbolic rhetoric of “cyber war” makes a lot more sense. The DoD views what we call the open Internet as a weapons system and/or potential existential threat because it uses its own networks and systems as a weapons system to impose existential threats upon other nations, sectarian groups, and American citizens.
Like the majority of the military-industrial complex, a lot of the DoD’s network infrastructure is built and maintained by contractors—not just telecoms like BT but also software and security companies. The trope of military contractors diversifying to police departments became well worn following the military drawdowns of Iraq and Afghanistan, but the focus is generally on tactical gear and military vehicles, not the infrastructure emerging in the wake of network-centric warfare. The concept of network-centric policing has so far been mainly associated with predictive policing research, but its rise has roots in both the acceleration of network-centric warfare and the emergence of the “smart city” paradigm.
Perhaps few cities were as adept at adopting network-centric law enforcement strategies as New York (which makes sense given that the city is basically the birthplace of data-driven policing and was dramatically shaped over 12 years by a billionaire mayor who made his fortune on proprietary data services). In 2010, New York City paid Northrop Grumman $549 million to build NYCWiN, a citywide public safety broadband wireless network (ironically, the NYPD has been slow to adopt for its own purposes but it’s proven pretty useful for other networked projects by the Department of Environmental Protection and the Parks Department). In 2012, the NYPD unveiled the Domain Awareness System, a massive partnership with Microsoft that centralized surveillance feeds and other networked services in the name of security. In 2014, the NYPD began a $1.5 million pilot program to implement ShotSpotter, a controversial networked sensor service that’s supposed to rapidly detect gunshots in urban areas (and, as was discovered in an incident in Massachusetts, can also detect and record voices). Most recently, the NYPD has begun to implement pilot programs equipping police officers with networked body cameras. The body camera program has its roots in the Floyd v. City of New York verdict that mandated dramatic changes to the NYPD’s stop-and-frisk policies, but its implementation has coincided with increasing demands across the country for police body cameras in the wake of the deaths of Eric Garner and Michael Brown.
As more and more police departments rush to equip their officers with body cameras, I think about that DISA quote from 2006. The leading proprietor of cop body cameras in the United States right now is Taser, the company that manufactures the stun guns of the same name. When it actually comes to business models, Taser’s camera setup is kind of brilliant. Cameras are fairly cheap to manufacture and likely to get cheaper, but data storage needs will only metastasize. Taser isn’t actually selling cameras so much as they’re selling cloud storage for camera data and a platform for accessing that data, rendering what might be commonly seen as an ethical or cultural problem (i.e., police accountability) into a data storage problem, a network infrastructure problem.
Defense Information Systems Agency (DISA). http://www.disa.mil/. Courtesy of the Internet.
Another increasingly popular instrument of network-centric policing is not itself infrastructure but the impersonation of it. Stingrays, a surveillance tool manufactured by military contractor Harris Corporation, capture unique data about cell phones by setting up a fake cell tower that phones connect to while searching for a signal. Combined with other technologies (also manufactured and sold by Harris), Stingrays can be used to eavesdrop on conversations and text messages. Disclosure about police use of Stingrays has been limited and efforts by groups like the ACLU to find out more about their use have hit a number of legal roadblocks. Although technically Stingrays are supposedly used in the service of trying to capture and intercept individuals’ communications, the devices aren’t designed to capture a single target—they’re IMSI (International Mobile Subscriber Identity) catchers, indiscriminately accepting and logging all cell phone data. Assuming the best of law enforcement, those other phones captured by a Stingray are collateral damage. Increasingly, it appears that they’re being used explicitly for dragnet surveillance in contexts like mass protests. Being within the reach of an IMSI catcher becomes enough pretext for surveillance. Network-centric policing not only militarizes network space, it also reinforces the militarization of physical space—and, returning to Appelbaum’s quote, demonstrates the fallacy of assuming there’s a clear distinction between the two.
There is no separation between the real world and the Internet, and there never has been. As the false boundaries between those spaces blur, similarly imagined boundaries between state and corporate interests, between infrastructure and weapons systems also reveal themselves to be fictitious. To some extent, the emergence of network-centric warfare and network-centric policing reflects a general shift toward a network-centric everything. And to an extent, both military and police are correct to perceive the network as a potential existential threat to their methods—not only because that’s how they’re using networks, but also because networks are being used to circumvent them. One of the reasons that recent protests against police violence in cities across America have so successfully shut down cities (blockading traffic, interrupting sporting events, disrupting shopping centers) is that they have been well networked yet still thoroughly decentralized. March routes are contingent, communicated mostly in the moment. Every evening I returned home from one of the protests following the non-indictment of Darren Wilson I was shocked at the number of actions that had been happening simultaneously to the march I’d attended.
This is where I continue to find hope in the face of an increasingly militarized Internet—in localized models, in the contingency of emergent systems. The way in which activists build and use networks is largely in opposition to the hyper-centralized, panoptic model of network-centric warfare. Part of this is simply a matter of scale. In the face of an increased militarization, policing, and weaponization of networked space, the act of building an entirely separate, global parallel network requires an act of secession—not merely in a figurative John Perry Barlow sense, but a heavy, physical, infrastructural one whose borders, frankly, will never be legitimized. We can’t just build a “new Internet” or demand a return to an early 1990s Internet that never was any more than we can wash our hands of or return to a United States of America that’s not inextricably tied to structural racism. But we can carve out pockets of opposition and contingency within the networks we have. To conceive of a future beyond a militarized network, one must remain illegible to it.